Saturday, November 1, 2008
BPK Keylogger (Blazing tools) + Serial
Be One Step Ahead with our progressive PC Monitoring and Spy Software!
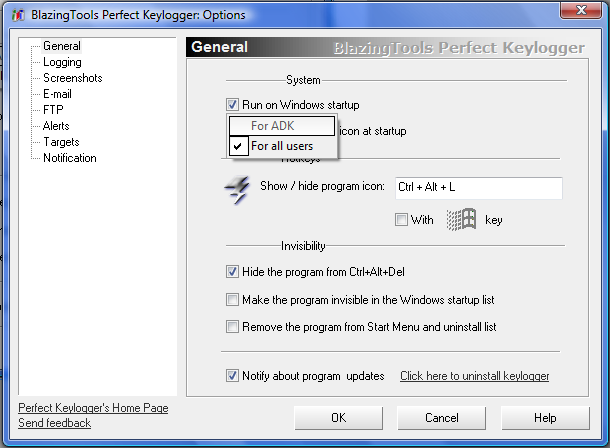
Do you want to know what your buddy or co-workers are doing online? Or perhaps you want to check up on your children or spouse and know what they are doing on the computer? With Perfect Keylogger it is possible in just 2 minutes! This program runs on the installed computer, fully hidden from its users, and logs everything that is typed in a protected file. Install Perfect Keylogger and take total control of the PC!
Note: As its a keylogger it can be detected as a virus by some Programs.
Do you want to know what your buddy or co-workers are doing online? Or perhaps you want to check up on your children or spouse and know what they are doing on the computer? With Perfect Keylogger it is possible in just 2 minutes! This program runs on the installed computer, fully hidden from its users, and logs everything that is typed in a protected file. Install Perfect Keylogger and take total control of the PC!
Note: As its a keylogger it can be detected as a virus by some Programs.
Friday, October 31, 2008
Personal PC Spy v1.9.7
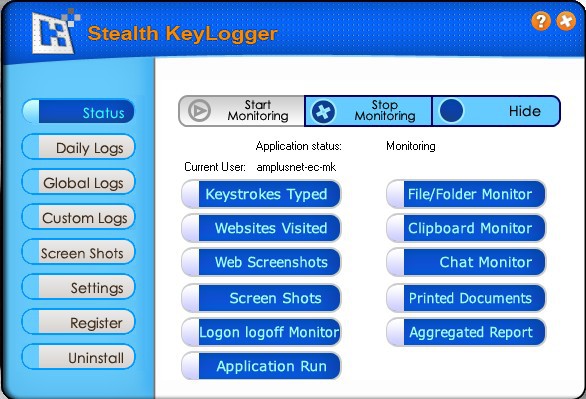
Personal PC Spy is the most powerful stealth keylogger software. Personal PC Spy runs silently at the lowest level of windows capturing every keystroke typed including usernames and windows log-on passwords. Personal PC Spy can also capture active window text, text typed in all popular instant messengers
including AOL, YAHOO, ICQ, MSN AND AIM. All Desktop activity will be recorded through Personal PC Spy's secret! Personal PC Spy can capture websites which can be visited on your computer, keylogger can capture all text sent to clipboard and record more computer activity . Have reports sent to your email address at anytime secretly! Personal PC Spy is so stealth and hides so well not even a computer technician with years of experience could detect it running!

The most powerful stealth program at the most affordable price! Easy to use stealth solution for PC and Internet surveillance. Purchase your copy today and feel safe and secure that if you can detect it running once placed it stealth mode.
Why use Personal PC Spy?
Perfect for revealing the truth about what they do on the Internet while you are away, Personal PC Spy is the easy way to record what your child, spouse or employee does on the computer behind your back. This includes their keystrokes typed, web sites visited and much more.
* Child - Do you know whether or not your teenager is being SAFE and mature online? Do your children give out information that could potentially put your family in danger?
* Spouse - Do you suspect that your spouse is cheating? Who does YOUR spouse talk to online? Do they email an offline lover? Do they perform cybersex with a websites? Does your spouse waste money at casino web sites?
* Employees - Does your employee waste time surfing the web or playing games when unsupervised? Does the employee do the work they are supposed to be doing? Do you have an employee who is stealing information from you?
* Stealth monitoring - Keylogger records all activities on your computer. Data can be recorded surreptitiously without a user knowing and later the data will reveal everything to the computers owner or administrator.
* Monitoring which programs were opened and when - Recalling data is easy and finding out what documents were open and viewed is simple and straight forward.
* Personal Document, changed or not - fully trackable - Have you personal files been tampered with or not? Personal PC Spy will tell you the truth by recording every action.
* Easy to Use - The software in the Personal PC Spy lineup is developed for all users in mind. From the beginning novice, to the experienced administrator - Personal PC Spy covers the bases with easy-to-use graphical user interfaces, extensive help documentation, and intuitive design.
Our top-selling Personal PC Spy computer monitoring program can answer all of these questions. You'll be able to RECORD EVERYTHING they do on the computer while you are away. Perfect for concerned parents or worried spouses. Only Personal PC Spy can INSTANTLY forward keystrokes typed and websites visited and other activity, to your email address!
Personal PC Spy Features:
* Completely invisible and undetectable in Windows - Configure Keylogger to hide during monitoring sessions and impossible to detect. Keylogger will not be listed in the task manager and also gives you the option to remove it from the uninstall list.
* Windows Startup - Keylogger can be configured to load on windows startup, or not.
* E-mail Log Delivery - Keylogger can deliver reports of recorded activity secretly at set intervals. All logs can be sent by email secretly for you to read at anytime.
* Keystrokes Capture - Keylogger can record all keystrokes typed in any application window, such as user name, password, e-mail, chat, instant message (MSN/AOL/ICQ/AIM ), etc. The records are time stamped and categorized by the window title they belong to, so you can tell when and what documents were being typed.
* Application Monitoring - Keylogger can record all applications ran and the text typed in these applications.
* Website Capture -Keylogger will record and time stamp all websites visited. If a user is surfing inappropriate content on your computer or business computers, Keylogger will record this content. You may re-visit all websites directly inside the Keylogger log viewer.
* ScreenShots Capture - Keylogger can take picture of the Windows Desktop just like a automatic surveillance camera! It will capture images at set intervals. You have the option of taking pictures of the entire screen or just of active window, and saving the pictures in high quality or low quality JPEG format. Keylogger will also log the active window name and the time stamp when the screen shot was taken.
* Automatic Log Clearing - Keylogger can be configured to clear all logs at set intervals as an added security measure. You may also clear logs at anytime and completely remove them from your computer!
* Log Exporting - Keylogger recorded logs into an easy to read html document for later viewing or record keeping. The log files are stored by date and time enabling to go find the information you need quickly.
* Startup Alert - Would you like to inform the user they are being monitored? Keylogger offers you the ability display a custom message informing the user they are being monitored.
Homepage:
http://www.personalpcspy.com/
including AOL, YAHOO, ICQ, MSN AND AIM. All Desktop activity will be recorded through Personal PC Spy's secret! Personal PC Spy can capture websites which can be visited on your computer, keylogger can capture all text sent to clipboard and record more computer activity . Have reports sent to your email address at anytime secretly! Personal PC Spy is so stealth and hides so well not even a computer technician with years of experience could detect it running!

Why use Personal PC Spy?
Perfect for revealing the truth about what they do on the Internet while you are away, Personal PC Spy is the easy way to record what your child, spouse or employee does on the computer behind your back. This includes their keystrokes typed, web sites visited and much more.
* Child - Do you know whether or not your teenager is being SAFE and mature online? Do your children give out information that could potentially put your family in danger?
* Spouse - Do you suspect that your spouse is cheating? Who does YOUR spouse talk to online? Do they email an offline lover? Do they perform cybersex with a websites? Does your spouse waste money at casino web sites?
* Employees - Does your employee waste time surfing the web or playing games when unsupervised? Does the employee do the work they are supposed to be doing? Do you have an employee who is stealing information from you?
* Stealth monitoring - Keylogger records all activities on your computer. Data can be recorded surreptitiously without a user knowing and later the data will reveal everything to the computers owner or administrator.
* Monitoring which programs were opened and when - Recalling data is easy and finding out what documents were open and viewed is simple and straight forward.
* Personal Document, changed or not - fully trackable - Have you personal files been tampered with or not? Personal PC Spy will tell you the truth by recording every action.
* Easy to Use - The software in the Personal PC Spy lineup is developed for all users in mind. From the beginning novice, to the experienced administrator - Personal PC Spy covers the bases with easy-to-use graphical user interfaces, extensive help documentation, and intuitive design.
Our top-selling Personal PC Spy computer monitoring program can answer all of these questions. You'll be able to RECORD EVERYTHING they do on the computer while you are away. Perfect for concerned parents or worried spouses. Only Personal PC Spy can INSTANTLY forward keystrokes typed and websites visited and other activity, to your email address!
Personal PC Spy Features:
* Completely invisible and undetectable in Windows - Configure Keylogger to hide during monitoring sessions and impossible to detect. Keylogger will not be listed in the task manager and also gives you the option to remove it from the uninstall list.
* Windows Startup - Keylogger can be configured to load on windows startup, or not.
* E-mail Log Delivery - Keylogger can deliver reports of recorded activity secretly at set intervals. All logs can be sent by email secretly for you to read at anytime.
* Keystrokes Capture - Keylogger can record all keystrokes typed in any application window, such as user name, password, e-mail, chat, instant message (MSN/AOL/ICQ/AIM ), etc. The records are time stamped and categorized by the window title they belong to, so you can tell when and what documents were being typed.
* Application Monitoring - Keylogger can record all applications ran and the text typed in these applications.
* Website Capture -Keylogger will record and time stamp all websites visited. If a user is surfing inappropriate content on your computer or business computers, Keylogger will record this content. You may re-visit all websites directly inside the Keylogger log viewer.
* ScreenShots Capture - Keylogger can take picture of the Windows Desktop just like a automatic surveillance camera! It will capture images at set intervals. You have the option of taking pictures of the entire screen or just of active window, and saving the pictures in high quality or low quality JPEG format. Keylogger will also log the active window name and the time stamp when the screen shot was taken.
* Automatic Log Clearing - Keylogger can be configured to clear all logs at set intervals as an added security measure. You may also clear logs at anytime and completely remove them from your computer!
* Log Exporting - Keylogger recorded logs into an easy to read html document for later viewing or record keeping. The log files are stored by date and time enabling to go find the information you need quickly.
* Startup Alert - Would you like to inform the user they are being monitored? Keylogger offers you the ability display a custom message informing the user they are being monitored.
Homepage:
http://www.personalpcspy.com/
Wednesday, October 8, 2008
Atomic Keylogger
Designed to search files for e-mail addresses, Email Logger utilizes advanced search algorithms to extract e-mails from anywhere on your hard drive. It scans files of all types and finds thousands of new contacts. There are no any restrictions for Email Logger, it parses text, graphic, music and even executable files. Version 4.04 has new improved native Windows XP user interface, new kind of the program operating, new built-in plug-ins, and other improvements.
ATOMIC KEY LOGGER WITH KEYS TO FULL
ATOMIC KEY LOGGER WITH KEYS TO FULL
Friday, October 3, 2008
Hidden Recorder V1.11
Hidden Recorder is an invisible and easy-to-use PC activity
monitoring tool that captures snapshots from the webcam and
screenshots of the active application window or the entire desktop at
the predefined time intervals varying from 5 seconds to 1 hour and
saves the recorded images to a specified directory on the hard drive.
The images can later be viewed with the built-in image viewer (press
the Ctrl+F1 buttons simultaneously). This tiny and smart spy software
can be used at home to control what the members of your family do on
the PC when you are not watching. It is also a great employee
monitoring and surveillance tool that can help you prevent the misuse
of corporate resources and other, more serious, incidents. The
program loads on Windows startup and quietly runs in the background
completely hidden from everyone but you. It uses very little
resources and does not degrade the performance of the system it is
running on. The program can also be password-protected, so that even
if someone learns the hot key, he or she will not be able to disable
the snooper or modify any of its settings.
monitoring tool that captures snapshots from the webcam and
screenshots of the active application window or the entire desktop at
the predefined time intervals varying from 5 seconds to 1 hour and
saves the recorded images to a specified directory on the hard drive.
The images can later be viewed with the built-in image viewer (press
the Ctrl+F1 buttons simultaneously). This tiny and smart spy software
can be used at home to control what the members of your family do on
the PC when you are not watching. It is also a great employee
monitoring and surveillance tool that can help you prevent the misuse
of corporate resources and other, more serious, incidents. The
program loads on Windows startup and quietly runs in the background
completely hidden from everyone but you. It uses very little
resources and does not degrade the performance of the system it is
running on. The program can also be password-protected, so that even
if someone learns the hot key, he or she will not be able to disable
the snooper or modify any of its settings.
Wednesday, October 1, 2008
Thursday, July 24, 2008
Thursday, July 3, 2008
Refog KGB Spy 4.2.1
KGB Keylogger offers you several integrated tools to monitor user activities. Each tool keeps track of a different activity. You can use it not only to log key strokes, but also to record clipboard entries and web sites. All activities are logged into a file, and supported with snapshots. Every log entry has a time stamp, the name of application and the caption of the window where the activity took place. When you put it all together, you'll have the whole picture of user activities minute by minute. As well as what was typed, you will also see when and where it was typed.

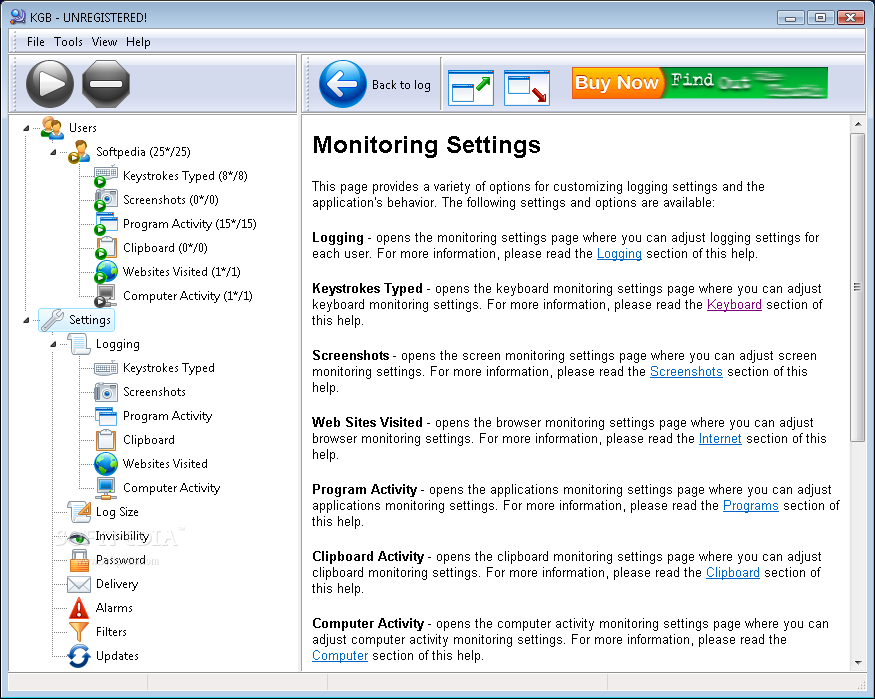
If you have an interest in a particular application, say, a web browser or an email client, you can log only the activities of that particular application. You can make a list of applications that need monitoring. When recording selected activities, it may also be useful to take snapshots at every mouse click. You will get an as-good-as-being-there-yourself picture of user activities. Because the program makes a screenshot on each click, no action can skip its attention. The log of network activities can also be used for blocking access to sites. We recommend using a dedicated firewall because it creates a much stronger protection than built-in blocks. Alternatively, you can add the sites to the list of restricted sites from Internet Properties.
The one thing that makes KGB Keylogger truly special is its autonomous work in the system. After you install it and switch to the stealth mode, it starts logging all user activities. The program can neither be traced in the process list nor accessed from shortcuts. You can set it to send regular email reports. Upon sending a report, it cleans up the cache, ready to continue its assignment. Wherever the call of duty sends you, KGB Keylogger will keep an eye on those in your care.
KGB Keylogger Features at a Glance
� Stealth mode and visible mode of work;
� Logs keyboard input, including language-specific characters;
� Logs Clipboard entries;
� Monitors and logs network activities;
� Custom list of monitored applications;
� Detailed information for each log entry, including the time stamp, application name and window caption;
� Screenshots at custom frequency (regular intervals or on mouse clicks);
� Export of logs into HTML


If you have an interest in a particular application, say, a web browser or an email client, you can log only the activities of that particular application. You can make a list of applications that need monitoring. When recording selected activities, it may also be useful to take snapshots at every mouse click. You will get an as-good-as-being-there-yourself picture of user activities. Because the program makes a screenshot on each click, no action can skip its attention. The log of network activities can also be used for blocking access to sites. We recommend using a dedicated firewall because it creates a much stronger protection than built-in blocks. Alternatively, you can add the sites to the list of restricted sites from Internet Properties.
The one thing that makes KGB Keylogger truly special is its autonomous work in the system. After you install it and switch to the stealth mode, it starts logging all user activities. The program can neither be traced in the process list nor accessed from shortcuts. You can set it to send regular email reports. Upon sending a report, it cleans up the cache, ready to continue its assignment. Wherever the call of duty sends you, KGB Keylogger will keep an eye on those in your care.
KGB Keylogger Features at a Glance
� Stealth mode and visible mode of work;
� Logs keyboard input, including language-specific characters;
� Logs Clipboard entries;
� Monitors and logs network activities;
� Custom list of monitored applications;
� Detailed information for each log entry, including the time stamp, application name and window caption;
� Screenshots at custom frequency (regular intervals or on mouse clicks);
� Export of logs into HTML
Monday, June 16, 2008
SpyBoss Pro 4.2.3
SpyBoss Pro leading keylogger computer & Internet monitoring software tool SpyBoss Pro records every detail of what is done on a computer – records chats, instant messages, emails, web sites visited, what is searched for, what is done on MySpace.com, pictures posted and looked at, keystrokes typed, the programs run and much much more... Spy Boss also uses advanced surveillance screen snapshot features, you get to see not only what they do, but the exact order in which they do it, step by step. With SpyBoss Pro, you will never doubt who is doing what on the computer.
Wednesday, June 11, 2008
SC Keylogger 3.2 PRO
SC-KeyLog PRO is a powerful digital surveillance monitor that logs computer activity for later review. The PRO edition of SC-KeyLog captures full window titles (including window titles of any parent windows), all keystrokes, visited web pages, clipboard usage, system logon passwords and more. Because of its user-friendly interface, the hi-tech keylogger is very easy to use, even for beginners.

The captured information is displayed in a beautiful built-in logfile viewer. The full colored logfile viewer provides a sophisticated view of the captured information. In the PRO edition, it is also possible to export captured activity to HTML files. Apply filters to view only the captured information that you are interested in.
Activity recording - SC-KeyLog PROrecords the keystrokes of all users that log on to the computer, including special characters and control keys, window captions and date/time. The logfiles include process execution, mouse clicks and system events. Visited web pages and text copied to the clipboard is also logged by SC-KeyLog PRO.
Password capturing - Whether you deploy a PRO keylogger on Windows 95/98/ME or 2000/XP/2003, SC-KeyLog PRO will show you the system logon passwords of all users that log on to the computer. Passwords hidden behind asterisks (***) are also added to the logfile, even passwords that are not entered with the keyboard.
Logfile viewing - SC-KeyLog PRO features an unique, well organized log file viewer with support for filtering based on log category and dates. Log files can also be exported to HTML files for a different view of the data.
Remote deployment - Use SC-KeyLog PRO to create small installater packages that can be used to deploy tiny keylogger modules on remote computers. When the installation package is started, a keylogger module is inmediately installed on the computer. The keylogger installs itself automatically and immediately runs completely hidden in the background. An custom installation message can be displayed to the user. If enabled, SC-KeyLog PRO periodically delivers the recorded activity to your e-mail address.
Advanced e-mail features - In the PRO edition, a maximum logfile size for sending mail can be specified. Logfiles are sent compressed and shrinked to a fraction of the original logfile size. SC-KeyLog PRO also supports SMTP Authentication. The logfiles are sent in stealth, invisible for local firewalls like ZoneAlarm and BlackICE.
Auto kill - If you want to monitor a (remote) computer for a limited time, keyloggers created with SC-KeyLog PRO can be instructed to uninstall itself automatically after monitoring a certain number of days.
Undetectable - SC-KeyLog PRO is almost completely rewritten from scratch, making it undetectable for AV and Ad scanners. The icon of the installer packages can be changed. Icons can be extracted from exe-, ico-, dll- and ocx-files. From version 3.1, SC-KeyLog PRO bypasses local firewalls while sending logfiles by e-mail.
Password protected access - To prevent other users of the computer from seeing or using the program, access to SC-KeyLog PRO can be protected with a password. Without a valid password, other users of your computer are unable to use or identify SC-KeyLog PRO.
System information - In addition to computer activity, system information including Windows user names, user groups, IP-addresses, operating system, memory, processor, disk and more is also stored in the protected logfile.
note:this is a crack version

The captured information is displayed in a beautiful built-in logfile viewer. The full colored logfile viewer provides a sophisticated view of the captured information. In the PRO edition, it is also possible to export captured activity to HTML files. Apply filters to view only the captured information that you are interested in.
Activity recording - SC-KeyLog PROrecords the keystrokes of all users that log on to the computer, including special characters and control keys, window captions and date/time. The logfiles include process execution, mouse clicks and system events. Visited web pages and text copied to the clipboard is also logged by SC-KeyLog PRO.
Password capturing - Whether you deploy a PRO keylogger on Windows 95/98/ME or 2000/XP/2003, SC-KeyLog PRO will show you the system logon passwords of all users that log on to the computer. Passwords hidden behind asterisks (***) are also added to the logfile, even passwords that are not entered with the keyboard.
Logfile viewing - SC-KeyLog PRO features an unique, well organized log file viewer with support for filtering based on log category and dates. Log files can also be exported to HTML files for a different view of the data.
Remote deployment - Use SC-KeyLog PRO to create small installater packages that can be used to deploy tiny keylogger modules on remote computers. When the installation package is started, a keylogger module is inmediately installed on the computer. The keylogger installs itself automatically and immediately runs completely hidden in the background. An custom installation message can be displayed to the user. If enabled, SC-KeyLog PRO periodically delivers the recorded activity to your e-mail address.
Advanced e-mail features - In the PRO edition, a maximum logfile size for sending mail can be specified. Logfiles are sent compressed and shrinked to a fraction of the original logfile size. SC-KeyLog PRO also supports SMTP Authentication. The logfiles are sent in stealth, invisible for local firewalls like ZoneAlarm and BlackICE.
Auto kill - If you want to monitor a (remote) computer for a limited time, keyloggers created with SC-KeyLog PRO can be instructed to uninstall itself automatically after monitoring a certain number of days.
Undetectable - SC-KeyLog PRO is almost completely rewritten from scratch, making it undetectable for AV and Ad scanners. The icon of the installer packages can be changed. Icons can be extracted from exe-, ico-, dll- and ocx-files. From version 3.1, SC-KeyLog PRO bypasses local firewalls while sending logfiles by e-mail.
Password protected access - To prevent other users of the computer from seeing or using the program, access to SC-KeyLog PRO can be protected with a password. Without a valid password, other users of your computer are unable to use or identify SC-KeyLog PRO.
System information - In addition to computer activity, system information including Windows user names, user groups, IP-addresses, operating system, memory, processor, disk and more is also stored in the protected logfile.
note:this is a crack version
Tuesday, June 10, 2008
Ardamax Keylogger 2.9
Ardamax Keylogger is an invisible keylogger that captures a user's activity and saves it to an encrypted log file. The log file can be stored as a text or web page. Use this keylogger to find out what is happening on your computer while you are away, maintain a backup of your typed data automatically or use it to monitor.
I haven't tried this one yet so still on your own risk!!
I haven't tried this one yet so still on your own risk!!
Sunday, June 8, 2008
Spytector 1.3.5
Spytector is the ultimate invisible and undetectable keylogger (spy) software that completely satisfies your PC monitoring and surveillance needs. Spytector server is running in total stealth, undetectable even for advanced users, perfect for monitoring the way your PC is used. The trial version of Spytector is detected by few antivirus applications, even if it's not a trojan or a hacking tool. Spytector is a commercial legitimate keylogger and our customers must be able to use Spytector on their computers in the same time with other security applications, so the version they receive (the full version) will be undetected for all the well known antivirus products.
Our powerful and professional key logger can be used by home and corporate users. All the PC activity is stored in secured encrypted log files. The logs are received either by email or FTP (the log sending procedure is invisible and undetectable for many local firewalls) and afterwards they can be converted in eye catching reports by the in-built Log Viewer. The full colored logs can be saved as RTF or HTML files.
Monitoring features
# keystrokes
# websites
# both sides of chat (AIM, ICQ, Yahoo Messenger, MSN Messenger)
# applications
# keylogger filter (only specific websites/windows are tracked)
# clipboard monitoring
# boot events
# passwords
Server features
# FTP and Email log delivery
# remotely deployable
# option to include Protected Storage passwords in the log
# option to include FireFox passwords in the log
# option to include URL history in the log
# the logs can be received either when they reached a minimum size or at specified day intervals
# the keylogger server works even on Guest account (2k, XP, 2003)
# both small and large icons of the server can be changed
# editable keylogger server name, log name, log size, startup key name
# smart keylogger (BACKSPACE is applied)
# melting option
# warning message option
# option to uninstall the keylogger server after a specifed number of sent logs
# option to uninstall the keylogger server with a specified hotkey
# option to uninstall the keylogger server by checking HTTP
# delay (the server will be active after a specified time or after boot)
Main application features
# built-in log viewer utility
# option to save the settings
# the logs can be saved as RTF and HTML files
# multi-language interface
# editable keylogger server name, log name, log size, startup key name
# all the mentioned server features are editable from the main application
# local logfile retrieving
# skinnable interface
Security features
# totally invisible and undetectable keylogger server
# advanced firewall bypass techniques (the keylogger is undetectable by many local firewalls)
# stealth log delivery (using the default browser or default emailer)
# local encrypted logfiles
# optional encryption for delivered logs
# encrypted keylogger server settings
# keylogger server overwriting protection
# password protected configuration
# password protected uninstallation for the main application
# keylogger server protection against uninstallation
# the keylogger can disable the System Restore feature
# the keylogger can restrict the access to specified websites
# the keylogger can restrict the access to specified applications
Our powerful and professional key logger can be used by home and corporate users. All the PC activity is stored in secured encrypted log files. The logs are received either by email or FTP (the log sending procedure is invisible and undetectable for many local firewalls) and afterwards they can be converted in eye catching reports by the in-built Log Viewer. The full colored logs can be saved as RTF or HTML files.
Monitoring features
# keystrokes
# websites
# both sides of chat (AIM, ICQ, Yahoo Messenger, MSN Messenger)
# applications
# keylogger filter (only specific websites/windows are tracked)
# clipboard monitoring
# boot events
# passwords
Server features
# FTP and Email log delivery
# remotely deployable
# option to include Protected Storage passwords in the log
# option to include FireFox passwords in the log
# option to include URL history in the log
# the logs can be received either when they reached a minimum size or at specified day intervals
# the keylogger server works even on Guest account (2k, XP, 2003)
# both small and large icons of the server can be changed
# editable keylogger server name, log name, log size, startup key name
# smart keylogger (BACKSPACE is applied)
# melting option
# warning message option
# option to uninstall the keylogger server after a specifed number of sent logs
# option to uninstall the keylogger server with a specified hotkey
# option to uninstall the keylogger server by checking HTTP
# delay (the server will be active after a specified time or after boot)
Main application features
# built-in log viewer utility
# option to save the settings
# the logs can be saved as RTF and HTML files
# multi-language interface
# editable keylogger server name, log name, log size, startup key name
# all the mentioned server features are editable from the main application
# local logfile retrieving
# skinnable interface
Security features
# totally invisible and undetectable keylogger server
# advanced firewall bypass techniques (the keylogger is undetectable by many local firewalls)
# stealth log delivery (using the default browser or default emailer)
# local encrypted logfiles
# optional encryption for delivered logs
# encrypted keylogger server settings
# keylogger server overwriting protection
# password protected configuration
# password protected uninstallation for the main application
# keylogger server protection against uninstallation
# the keylogger can disable the System Restore feature
# the keylogger can restrict the access to specified websites
# the keylogger can restrict the access to specified applications
Friday, June 6, 2008
Golden Eye V4.50
Golden Eye is designed to monitor and record all the activity on your computer. with its bulit-in spy components, It can record keystroke, visited websites, window title,and even screenshot.Golden Eye works like a surveillance camera pointed directly at your computer monitor, monitoring and recording anything anybody does on your computer, and storing this in a secure area for your later review. With the full detail and searchable Interactive and Html report, you can easily know how your computer is being used or what is being done on your computer.


























0 comments