hursday, October 30, 2008
Thursday, October 23, 2008
Real Spy Monitor V2.87 WinAll
Real Spy Monitor can monitor all PC activity including keystrokes typed, web sites visited, windows opened, program executed, screen snapshots, files/docs accessed and more. It can also record instant messenger conversations including AOL, ICQ, MSN, AIM, Yahoo Messenger, and capture web mail content from MSN, Hotmail, and Yahoo. The program can run in semi-stealth mode (visible in Task Manager) and automatically send logs to a specified email address. Additional features include screenshot capture and content filtering. The program does not include any ********ation. Because it is sold commercially, most anti-virus vendors do not detect them. The most common form of a commercial monitoring tool comes in the form of a keystroke logger, which intercepts keystrokes from the keyboard and records them in some form of a log. This can then be sent to whoever installed the keystroke logger, or keylogger, onto the machine.

Worried about how your PC is being used? Want to keep tabs on your children, spouse, employees? Need to Prevent your children or employee from some application or web sites? Real Spy Monitor is the full solution for you.
For example, you can use Real Spy Monitor to:
- Monitor Keystrokes typed, Websites visited, Windows viewed, Program executed, Screen snapshots, Files/Docs accessed.
- Log Internet Chat conversation including AOL/ICQ/MSN/AIM Instant Messengers
- Spy Web Mail Content including MSN/HotMail, Yahoo! Mail
- Prevent your children or employee from some application or websites that include special keywords.
- When you left your your PC, Record your PC actions and send them through Email delivery at set times.
What's New in Real Spy Monitor Build 2.87
1 Reduces CPU occupancy to lower than 15%
2 Fixes the bug when it can't be loaded when Windows Startup
3 Hides application name of itself in Windows2000/XP
4 Fixes the bug on "e-mail delivery"
5 Supports to spy the newest version of MSN Messenger 6.1
6 Optimizes the code to avoid Unknown error
7 Redesigns all the graphic user interface;
8 Redesigns html report, see the example [Keystrokes] [Websites]
9 Html report supports to view snapshots directly
10 Save the html report with snapshots to local disk directly
11 Redesigns Messenger HTML report
12 Fixes the bug on Messenger HTML report delivery
13 Supports to remove/restore icon from Desktop, Start Menu, Add/Remove Program
14 Start Real Spy Monitor click on Start, Run, typed in "realspy"
15 If administrator remove the icon, the program cannot be uninstalled without password.
16 Adds a warning to user that they are monitored on start up. The **** can be changed in the control panel by the administrator.
17 Adds a "Test Now" button to test whether the SMTP Mail Host works or not.
18 Supports nearly all the available SMTP mail hosts.
19 Reduces CPU occupancy to lower than 5%
20 Improve the function of "File/Doc Access", you can record all the file-operation now, such as create, delete, update files or folders etc.
21 Supports to close the splash warning in ten seconds automatically
22 Supports to deliver logs via FTP now!
23 Rewrite the core code to avoid "RUN-TIME ERROR"
24 Improve the uninstall program.
25 Rewrite the setup program and reduce the size of it.
26 Supports to delete all the logs in system when you uninstall the program.
27 Hides installing path to avoid to be found.
28 Fix the bug "Run time error '75'acht/File access error" for win2000&winXP user under NTFS disk
29 Rewrite the core code to support Windows XP SP2
30 Optimizes the code for win98 to avoid setacl.ocx missing error
31 Names logs as "rsm@date.html" format to deliver via FTP
32 Rewrites the core code to avoid being scanned as virus or spyware mistakenly.
33 Supports to spy the newest version of MSN Messenger 7.0
34 Supports to spy the newest explorer version IE7

Worried about how your PC is being used? Want to keep tabs on your children, spouse, employees? Need to Prevent your children or employee from some application or web sites? Real Spy Monitor is the full solution for you.
For example, you can use Real Spy Monitor to:
- Monitor Keystrokes typed, Websites visited, Windows viewed, Program executed, Screen snapshots, Files/Docs accessed.
- Log Internet Chat conversation including AOL/ICQ/MSN/AIM Instant Messengers
- Spy Web Mail Content including MSN/HotMail, Yahoo! Mail
- Prevent your children or employee from some application or websites that include special keywords.
- When you left your your PC, Record your PC actions and send them through Email delivery at set times.
What's New in Real Spy Monitor Build 2.87
1 Reduces CPU occupancy to lower than 15%
2 Fixes the bug when it can't be loaded when Windows Startup
3 Hides application name of itself in Windows2000/XP
4 Fixes the bug on "e-mail delivery"
5 Supports to spy the newest version of MSN Messenger 6.1
6 Optimizes the code to avoid Unknown error
7 Redesigns all the graphic user interface;
8 Redesigns html report, see the example [Keystrokes] [Websites]
9 Html report supports to view snapshots directly
10 Save the html report with snapshots to local disk directly
11 Redesigns Messenger HTML report
12 Fixes the bug on Messenger HTML report delivery
13 Supports to remove/restore icon from Desktop, Start Menu, Add/Remove Program
14 Start Real Spy Monitor click on Start, Run, typed in "realspy"
15 If administrator remove the icon, the program cannot be uninstalled without password.
16 Adds a warning to user that they are monitored on start up. The **** can be changed in the control panel by the administrator.
17 Adds a "Test Now" button to test whether the SMTP Mail Host works or not.
18 Supports nearly all the available SMTP mail hosts.
19 Reduces CPU occupancy to lower than 5%
20 Improve the function of "File/Doc Access", you can record all the file-operation now, such as create, delete, update files or folders etc.
21 Supports to close the splash warning in ten seconds automatically
22 Supports to deliver logs via FTP now!
23 Rewrite the core code to avoid "RUN-TIME ERROR"
24 Improve the uninstall program.
25 Rewrite the setup program and reduce the size of it.
26 Supports to delete all the logs in system when you uninstall the program.
27 Hides installing path to avoid to be found.
28 Fix the bug "Run time error '75'acht/File access error" for win2000&winXP user under NTFS disk
29 Rewrite the core code to support Windows XP SP2
30 Optimizes the code for win98 to avoid setacl.ocx missing error
31 Names logs as "rsm@date.html" format to deliver via FTP
32 Rewrites the core code to avoid being scanned as virus or spyware mistakenly.
33 Supports to spy the newest version of MSN Messenger 7.0
34 Supports to spy the newest explorer version IE7
Friday, October 3, 2008
Remote Administrator Control 3.3.1 - Awarded Remote Access Soft
Remote Administrator Control 3.3.1 | 5.53 MB
Radmin (Remote Administrator) is the world famous, award winning secure remote control software and remote access software which enables you to work on a remote computer in real time as if you were using its own keyboard and mouse.
Features:
- Safe and fast computer control through Internet/Intranet network with TCP/IP protocol
- Computer administration and maintenance, e.g. on administrator or management workplaces
- User support and problem solution, e.g. helpdesk workplaces
- Observing teaching in computer classes
- File and folder transfer
- Activity recording when controlling a computer
- Activity monitoring or recording on a remote computer
- Starting commands and tools on a remote system
- Access to home computer from work through HTTP tunnel
- Access to work computer from home or another private network through HTTP tunnel
Supported Operating Systems:
- Windows® 95
- Windows® 98
- Windows® ME
- Windows NT® 4.0
- Windows® 2000
- Windows® XP (32/64-bit)
- Windows® Server 2003 (32/64-bit)
- Windows Vista™ (32/64-bit)
Radmin (Remote Administrator) is the world famous, award winning secure remote control software and remote access software which enables you to work on a remote computer in real time as if you were using its own keyboard and mouse.
Features:
- Safe and fast computer control through Internet/Intranet network with TCP/IP protocol
- Computer administration and maintenance, e.g. on administrator or management workplaces
- User support and problem solution, e.g. helpdesk workplaces
- Observing teaching in computer classes
- File and folder transfer
- Activity recording when controlling a computer
- Activity monitoring or recording on a remote computer
- Starting commands and tools on a remote system
- Access to home computer from work through HTTP tunnel
- Access to work computer from home or another private network through HTTP tunnel
Supported Operating Systems:
- Windows® 95
- Windows® 98
- Windows® ME
- Windows NT® 4.0
- Windows® 2000
- Windows® XP (32/64-bit)
- Windows® Server 2003 (32/64-bit)
- Windows Vista™ (32/64-bit)
Thursday, September 25, 2008
Thursday, September 18, 2008
AdminToys.Suite.2008.1.1.1100-NoPE

AdminToys Suite is a collection of administration utilities
for remote management of Windows Servers and Workstations.
AdminToys Suite comes with 13 network tools that help you
to save time on everyday administrative tasks: Remote
Process Manager, Remote System Manager, Data Storage
Information, Remote Disk Quota Manager, Remote Registry
Manager, Remote Daemon Manager, Remote Event Log Manager,
Remote IP Configuration, Batch Clock Synchronization, Batch
Remote Power Off, Batch Remote Restart, Batch Remote Log
Off, Batch Command Execution. AdminToys Suite modules
allows you dump the result to TXT or CSV file, or create a
printable HTML report.


pass:Drav3n
Nuclear RAT V2.1.0
feature highlight:
>> unicode support, you can see folders, windows, text, in any world language, that windows can support. tested with korean, japanese, arabian, vietnamese, chinese, portuguese, spanish, russian, and more! (check the screenshot)
>> very fast and secure listings (for windows, file manager, network manager, etc). navigate through the remote computer hdd like if you were opening on your local computer! use the "go to" commands to reach the folder you want, perfectly fast. the same applies to the registry!
>> improved keylogger, you won't have problems with double accents (~~, ´´), get a smooth result from the keylogger, and easy to read text.
>> network manager allows you to browse the other computers in the same lan (that are already authenticated), upload, download and delete files from those other computers in lan! no need for installing a server on another pc (just to browse the lan shares)
>> hybrid support for both direct and reverse connection modes. you can receive connections on your client at the same time you connect to direct connection servers
>> huge list of possibilities for process injection, decide where to inject your server, where to install, startup methods, and have full control over your server creation. inject to default browser, custom windows, start any type of program, inject to winsock enabled applications, inject to all applications, etc
>> multiple transfers at once (multi-threaded) or queue transfers system.
>> very powerful plugin system, where you may add anything your mind could think of. add netlimiters, socks, encryption, rootkits, compression, password stealers, cd key stealers, offline keyloggers, anything!
>> support for very big files, up to 5 pb
>> intrinsic help system, clicking the "?" will help you understand certain functions from the program
>> multi language support for the client, see the program on your primary language (should be available soon)
>> filemanager with quick edit feature: edit plain text files without having to download them and upload again! also, there's a new "create new file" feature, makes you able to create new files quickly, without having to upload a new file!
>> all transfers have "resume" feature, even network transfers. resume folder downloads, uploads, downloads and network uploads and downloads
>> very fast ip scanner, use the remote machine to execute ip range scans for you
>> two other new revamped features: connection bouncer and remote service reacher. those improved functions will help you to reach the remote computer services that doesn't allow direct connections from wan

after the feature highlight, now the almost full feature list:
- screenshot with png compression, save to file, auto-rename, send mouse motions to the screen, enable timer
- webcam shot with png compression, save to file, auto-rename, enable timer
- keylogger with support to accents and language specific symbols
- computer information with valuable information about the computer
- mouse control with get/set position, get text under mouse cursor
- screen resolutions, turn off/on monitor
- socks5 daemon
- http fileserver, with unicode support. browse the computer hdd using your browser, and download files as well.
- remote shell with support for either ansi and unicode (windows xp won't allow unicode support natively)
- file manager with: download folder, download file, upload file, quick edit, create new file, properties, live search files, go to path, open, run hidden, play mid/wav files, copy, move, rename, delete, map network drive, create folder, delete folder, bookmarks to "system32", "windows", "my documents", etc, open/close cd tray, and much more. attention: very fast
- window manager with a lot of features, like hide/show, enable/disable x, rename caption, and send keys to window
- process manager, with module (dlls) manager, with inject and uninject capabilities
- registry manager with all types of registry types, reg_sz, reg_multi_sz, reg_dword, reg_binary, reg_none, etc (improved)
- transfer manager with two modes, queue and transfer all at once
- clipboard manager with unicode support like it should
- plugins manager
- connections (inspect the connections that the client is currently receiving)
- remote connections (inspect the connections that the server is currently making)
- network manager with download/upload/delete files from the same lan without the need of a server on the other computers
- shutdown/restart/log off computer
- message box
- multiple threaded web download
- fast ip range scanner
- chat to remote computer built-in, with unicode support, on both sides!
- raw shellexecute api, to perform any type of shell operation you wish
- connection bouncer (former port redirect)
- remote service reacher (former tcp tunnel)
- quick menu where you can even link outside programs, files, anything!
tons of configurations, this list is almost full, although there are a lot more features to explore
from the file changelog.txt
legend:
+ addition
- removal
* bug fix
> improvement
v. 2.1.0 (september 4th):
* stealth shell folder startup
* active setup startup
* filemanager file listing were incomplete on some computers
* uninstallation
+ multiple dns support
* ip via url
* persistent systray icon
> injection methods
+ bind plugins
> plugin management
- vbs instalation of startup method
> server size
* clipboard manager (was 'eating' the last character')
* remote connections for reverse servers
> check version
* random crash/hang upon selecting a server on the list
* random lockups
* access violation when downloading multiple files using network manager
> check for new version
* some issues with 64bit processors and os
* problem with "ilfree" symbol on win2k computers
* some issues with windows vista
+ sort servers according to column
* change.php script
* unicode logging
* popup notification
* command line plugin answer support
> server extensions support
+ server version column on server list
note: the filemanager, to work properly, must have the server updated!
some functions will need a new client for it to work properly, so always
keep the program up-to-date
>> unicode support, you can see folders, windows, text, in any world language, that windows can support. tested with korean, japanese, arabian, vietnamese, chinese, portuguese, spanish, russian, and more! (check the screenshot)
>> very fast and secure listings (for windows, file manager, network manager, etc). navigate through the remote computer hdd like if you were opening on your local computer! use the "go to" commands to reach the folder you want, perfectly fast. the same applies to the registry!
>> improved keylogger, you won't have problems with double accents (~~, ´´), get a smooth result from the keylogger, and easy to read text.
>> network manager allows you to browse the other computers in the same lan (that are already authenticated), upload, download and delete files from those other computers in lan! no need for installing a server on another pc (just to browse the lan shares)
>> hybrid support for both direct and reverse connection modes. you can receive connections on your client at the same time you connect to direct connection servers
>> huge list of possibilities for process injection, decide where to inject your server, where to install, startup methods, and have full control over your server creation. inject to default browser, custom windows, start any type of program, inject to winsock enabled applications, inject to all applications, etc
>> multiple transfers at once (multi-threaded) or queue transfers system.
>> very powerful plugin system, where you may add anything your mind could think of. add netlimiters, socks, encryption, rootkits, compression, password stealers, cd key stealers, offline keyloggers, anything!
>> support for very big files, up to 5 pb
>> intrinsic help system, clicking the "?" will help you understand certain functions from the program
>> multi language support for the client, see the program on your primary language (should be available soon)
>> filemanager with quick edit feature: edit plain text files without having to download them and upload again! also, there's a new "create new file" feature, makes you able to create new files quickly, without having to upload a new file!
>> all transfers have "resume" feature, even network transfers. resume folder downloads, uploads, downloads and network uploads and downloads
>> very fast ip scanner, use the remote machine to execute ip range scans for you
>> two other new revamped features: connection bouncer and remote service reacher. those improved functions will help you to reach the remote computer services that doesn't allow direct connections from wan

after the feature highlight, now the almost full feature list:
- screenshot with png compression, save to file, auto-rename, send mouse motions to the screen, enable timer
- webcam shot with png compression, save to file, auto-rename, enable timer
- keylogger with support to accents and language specific symbols
- computer information with valuable information about the computer
- mouse control with get/set position, get text under mouse cursor
- screen resolutions, turn off/on monitor
- socks5 daemon
- http fileserver, with unicode support. browse the computer hdd using your browser, and download files as well.
- remote shell with support for either ansi and unicode (windows xp won't allow unicode support natively)
- file manager with: download folder, download file, upload file, quick edit, create new file, properties, live search files, go to path, open, run hidden, play mid/wav files, copy, move, rename, delete, map network drive, create folder, delete folder, bookmarks to "system32", "windows", "my documents", etc, open/close cd tray, and much more. attention: very fast
- window manager with a lot of features, like hide/show, enable/disable x, rename caption, and send keys to window
- process manager, with module (dlls) manager, with inject and uninject capabilities
- registry manager with all types of registry types, reg_sz, reg_multi_sz, reg_dword, reg_binary, reg_none, etc (improved)
- transfer manager with two modes, queue and transfer all at once
- clipboard manager with unicode support like it should
- plugins manager
- connections (inspect the connections that the client is currently receiving)
- remote connections (inspect the connections that the server is currently making)
- network manager with download/upload/delete files from the same lan without the need of a server on the other computers
- shutdown/restart/log off computer
- message box
- multiple threaded web download
- fast ip range scanner
- chat to remote computer built-in, with unicode support, on both sides!
- raw shellexecute api, to perform any type of shell operation you wish
- connection bouncer (former port redirect)
- remote service reacher (former tcp tunnel)
- quick menu where you can even link outside programs, files, anything!
tons of configurations, this list is almost full, although there are a lot more features to explore
from the file changelog.txt
legend:
+ addition
- removal
* bug fix
> improvement
v. 2.1.0 (september 4th):
* stealth shell folder startup
* active setup startup
* filemanager file listing were incomplete on some computers
* uninstallation
+ multiple dns support
* ip via url
* persistent systray icon
> injection methods
+ bind plugins
> plugin management
- vbs instalation of startup method
> server size
* clipboard manager (was 'eating' the last character')
* remote connections for reverse servers
> check version
* random crash/hang upon selecting a server on the list
* random lockups
* access violation when downloading multiple files using network manager
> check for new version
* some issues with 64bit processors and os
* problem with "ilfree" symbol on win2k computers
* some issues with windows vista
+ sort servers according to column
* change.php script
* unicode logging
* popup notification
* command line plugin answer support
> server extensions support
+ server version column on server list
note: the filemanager, to work properly, must have the server updated!
some functions will need a new client for it to work properly, so always
keep the program up-to-date
Friday, September 12, 2008
UltraVNC 1.0.5
UltraVNC is an easy to use software that can display the screen of another computer (via internet or network) on your own screen. The program allows you to use your mouse and keyboard to control the other PC remotely. It means that you can work on a remote computer, as if you were sitting in front of it, right from your current location. If you provide computer support, you can easy access your customerґs computers from anywhere in the world and resolve helpdesk issues remotely ! Your customers donґt have to pre-install software or execute complex procedures to get remote helpdesk support. UltraVNC allows you to remotely control a computer over any TCP/IP connection. UltraVNC emulates the destination computer to make it look as if you were in front of it.
Wednesday, June 25, 2008
Wednesday, June 11, 2008
Radmin 3.2
Radmin (Remote Administrator) is fast and secure remote control and remote access software that enables you to work on a remote computer as if you were sitting right in front of it and access it from multiple places. Radmin includes full support for Windows Vista (32-bit and 64-bit), file transfer, multi-user text and voice chats, Windows security, Kerberos authentication, 256-bit AES encryption for all data streams, telnet access, multiple monitors support and unique DirectScreenTransfer? technology. Radmin utilizes the ever-present TCP/IP protocol - the most widespread protocol used in LANs, WANs and the Internet. This means you can access your remote computer from anywhere in the world. Radmin is deployed on thousands of corporate PCs worldwide. Among our clients are companies where Radmin is the standard application for network management.
You view the remote computer screen on your own monitor either in a window or full screen. All your mouse movements and keyboard signals are transferred directly to the remote computer. Radmin enables you to work on a remote computer in real time as if you were using its own keyboard and mouse. According to our tests and user feedback, Radmin outperforms all other remote control software in speed, usability and features.
You view the remote computer screen on your own monitor either in a window or full screen. All your mouse movements and keyboard signals are transferred directly to the remote computer. Radmin enables you to work on a remote computer in real time as if you were using its own keyboard and mouse. According to our tests and user feedback, Radmin outperforms all other remote control software in speed, usability and features.
Saturday, June 7, 2008
Network LookOut Administrator Pro 2.7.7
The Network LookOut Administrator Professional allows you to see live screens of remote computers. This way, you can always watch what users are doing on the remote computer. Additionally, you have the ability to take control of a remote computer by controlling the mouse and keyboard; this is especially useful when you need to assist the person who uses the remote computer. If you are an administrator, you can easily administer remote computers from your computer. To increase your efficiency the console now include several tolls that can be executed on all or just selected remote computers. Application works through Internet, LAN, WLAN or VPN. Agent can be remotely installed. Communication uses encrypted data streams.
What does it do?
It allows you to see live screens of remote computers. This way, you can always watch what users are doing on the remote computer. Additionally, you have the ability to take control of a remote computer by controlling the mouse and keyboard; this is especially useful when you need to assist the person who uses the remote computer. If you are an administrator, you can easily administer remote computers from your computer.
What is new in this release?
* Agent can be remotely installed.
* Encrypted data streams
What is it useful for?
* For monitoring your children’s activities on a remote computer.
* For monitoring students in the classroom to achieve better discipline or, just to assist them (by using the remote control feature) when they are in trouble.
* For lowering your business costs by monitoring what your employees are doing on their computers and helping them when they call you. Using the remote control feature enables you to fix problems remotely without visiting them; this saves you precious time.
* For administrating all computers just from one location – your computer.
* Turning off, restarting, hibernating .... remote computers with one click.
What are the major benefits of using Network LookOut Administrator Professional?
* Installation and use of the application is very easy since all of the functions can be accessed with a few mouse clicks.
* You have complete control over what remote users are doing.
* Unlike other similar applications, this application provides you with a live picture of the remote computer screens. The live screen (due to some optimizations) does not use a high bandwidth, but even when the lower network bandwidth is required the refresh interval can be enlarged using one mouse click.
* Unlike other similar applications, this application allows you to take over the remote computer by controlling its mouse and keyboard.
* The remote computers´ screens are represented in the table with a customizable number of rows as thumbnails.
* Using this application, you can always see which user is actually logged on to the remote computer.
* Execute several actions on all remote computers with on click
Main Features:
* Displaying a live picture of a remote computer.
* You can take control of a remote computer by controlling its mouse and keyboard.
* More remote screens can be displayed in a table.
* A remote screen can be zoomed to an actual size.
* The name of the connected user is displayed.
* When lower bandwidth is required, the refresh interval can be enlarged.
* Power off, restart, hibernate, suspend remote computers
* Log off desktop users
* Lock workstation
* Control screensaver
* Automatic connection to a remote computer is optional.
* Settings for the agent are encrypted and password protected.
* Connection to a remote computer is password protected.
* Access to monitoring the console is password protected. If more users use the same computer, different profiles and access passwords can be set.
* More monitoring consoles can be connected to the same remote computer.
* Agent can run as an NT service (for Windows NT, 2000, XP, 2003).
* Agent can run as a process (Windows 95, 98, Me).
* Application can optionally use encrypted communication.
* Agent can be remotely installed.
Install Notes
1. Run the setup.
2. Register your copy with a serial from the keygen, and now you have the licenses to add PC's.
3. Enjoy your remote monitoring!
P.S. The PCs you want to monitor, only need to have the agent installed, and not the Professional Console.
Install the console only to the PC you want to monitor all the other PCs from.
What does it do?
It allows you to see live screens of remote computers. This way, you can always watch what users are doing on the remote computer. Additionally, you have the ability to take control of a remote computer by controlling the mouse and keyboard; this is especially useful when you need to assist the person who uses the remote computer. If you are an administrator, you can easily administer remote computers from your computer.
What is new in this release?
* Agent can be remotely installed.
* Encrypted data streams
What is it useful for?
* For monitoring your children’s activities on a remote computer.
* For monitoring students in the classroom to achieve better discipline or, just to assist them (by using the remote control feature) when they are in trouble.
* For lowering your business costs by monitoring what your employees are doing on their computers and helping them when they call you. Using the remote control feature enables you to fix problems remotely without visiting them; this saves you precious time.
* For administrating all computers just from one location – your computer.
* Turning off, restarting, hibernating .... remote computers with one click.
What are the major benefits of using Network LookOut Administrator Professional?
* Installation and use of the application is very easy since all of the functions can be accessed with a few mouse clicks.
* You have complete control over what remote users are doing.
* Unlike other similar applications, this application provides you with a live picture of the remote computer screens. The live screen (due to some optimizations) does not use a high bandwidth, but even when the lower network bandwidth is required the refresh interval can be enlarged using one mouse click.
* Unlike other similar applications, this application allows you to take over the remote computer by controlling its mouse and keyboard.
* The remote computers´ screens are represented in the table with a customizable number of rows as thumbnails.
* Using this application, you can always see which user is actually logged on to the remote computer.
* Execute several actions on all remote computers with on click
Main Features:
* Displaying a live picture of a remote computer.
* You can take control of a remote computer by controlling its mouse and keyboard.
* More remote screens can be displayed in a table.
* A remote screen can be zoomed to an actual size.
* The name of the connected user is displayed.
* When lower bandwidth is required, the refresh interval can be enlarged.
* Power off, restart, hibernate, suspend remote computers
* Log off desktop users
* Lock workstation
* Control screensaver
* Automatic connection to a remote computer is optional.
* Settings for the agent are encrypted and password protected.
* Connection to a remote computer is password protected.
* Access to monitoring the console is password protected. If more users use the same computer, different profiles and access passwords can be set.
* More monitoring consoles can be connected to the same remote computer.
* Agent can run as an NT service (for Windows NT, 2000, XP, 2003).
* Agent can run as a process (Windows 95, 98, Me).
* Application can optionally use encrypted communication.
* Agent can be remotely installed.
Install Notes
1. Run the setup.
2. Register your copy with a serial from the keygen, and now you have the licenses to add PC's.
3. Enjoy your remote monitoring!
P.S. The PCs you want to monitor, only need to have the agent installed, and not the Professional Console.
Install the console only to the PC you want to monitor all the other PCs from.
Sunday, May 25, 2008
Remote Administrator Control 3.3.1
Features:
- Safe and fast computer control through Internet/Intranet network with TCP/IP protocol
- Computer administration and maintenance, e.g. on administrator or management workplaces
- User support and problem solution, e.g. helpdesk workplaces
- Observing teaching in computer classes
- File and folder transfer
- Activity recording when controlling a computer
- Activity monitoring or recording on a remote computer
- Starting commands and tools on a remote system
- Access to home computer from work through HTTP tunnel
- Access to work computer from home or another private network through HTTP tunnel
- Safe and fast computer control through Internet/Intranet network with TCP/IP protocol
- Computer administration and maintenance, e.g. on administrator or management workplaces
- User support and problem solution, e.g. helpdesk workplaces
- Observing teaching in computer classes
- File and folder transfer
- Activity recording when controlling a computer
- Activity monitoring or recording on a remote computer
- Starting commands and tools on a remote system
- Access to home computer from work through HTTP tunnel
- Access to work computer from home or another private network through HTTP tunnel
Monday, May 19, 2008
Remote Hacking
In this tutorial; you will learn how to access a computer's friend through a simple conversation on MSN. Its quite easy, but most people consider the contents of this document to be more of a 'script kiddie' actions.
Script Kiddie: n00b-hackers who consider themselfes to be powerful because of the tools they have obtained rather then the hard powerful way real hackers use.
But anyways, script kiddies <3
Okay, first of all, when downloading any kind of hacking or cracking executables or ZIPs then you must consider immediatly disabling your antivirus so it wont pick it up as a 'trojan' or a 'backdoor' or most common, a '.hacktool'
Method
The method we are using is called trojanning or setting a backdoor to your victim's computer. Backdoor(s) allow hackers to control your computer as if you asked them for remote assistance. 'Trojans' and / or 'backdoors' are quite named as a RAT (remote administration tools) or (remote access tools) in the hacking community.
How RAT(s) work
Simple question yet by a simple person; how do RAT(s) work. Well, they open a specific port on the victim's computer which allows any hacker to portscan the computer and see that this port is open, so he tries to connect to it and he gets access.
Okay, you might be saying wtf? What's a port, IP address and a portscan attack will be discussed shortly.
Glossary
IP address: IP addresses are your friend's internet address. If he's on dial-up, it changes on every reconnection to the internet (dynamic). On a broadband or highspeed connection, its static meaning it wont change.
Port: Consider a port more of a seaport; but the computers' has over 65,000 ports (65353 ports to be exact) and all of them are closed. Seaports allow ships to come in and out, if its closed, no ship is allowed to get in; its usually closed when a enemy or another country wants to enter the seaport.
Same as a computer's ports; they are closed when you are disconnected, when you connect, some are opened, and the hacker (enemy) is trying to get in, how will he know out of 65353 ports which one is open? Sure, he's not going to take a thousand year to try daily to connect to you on each port, his ISP will suspend him, you will track him and get him in jail even!
So he performs a...
Portscan attack: Portscanners launch a portscan attack on remote-computers to find out which ports are opened, and what service they are using to keep them open. Ports are opened for a reason, to allow data to come in and out, if you use firefox or internet explorer, port 80 is opened, etc. If you use mailservice; port 25 will be opened, etc.
If you haven't understand everything, which I dont blame you for because its alot of information; I suggest reading this tutorial after picking up a few TCP/IP and networking books and reading 'em to get deeper into the hacking community.
MSN convo -- 0wn3d
How will you know what is your friend's IP address, hm... There are a few methods hackers use targeting computer experts, but if your friend is dumb, or you're at his house, you might wanna go to whatismyip.com and writing it down on a piece of paper; or, you can ask him and tells him its a lucky number, type it for me in the MSN conversation.
If he's a computer expert or didn't fall for this, you might wanna try the hard way, send him any folder, doesn't have to be infected or a virus, make sure no conversations, applications, browsers, or anything that interepets or communicates with the internet is opened other then the conversation with your victim, Start -> Run... and type 'cmd.exe', type 'netstat -n' whilst sending the file and you will have a list of IP addresses. The first few are yours, now scroll down, and you see his 'foregin IP', write it down on a paper.
Yeah! You got his fricken' IP address! Now, lets perform our hacking!
Hacking Operation
Okay, well you know your friend's IP address. Aint that great? Lets perform our 411-hacking operation! okey: Poke your friend in the heart, yeah!
Okay, I got a bit hyper writing this tutorial till here, now lets continue.
Go to
http://library.2ya.com
and browse to: Trojans/Backdoors >> Trojan Horses >> Yuri RAT.
Now download Yuri RAT. Trojans work as a client/server direct-connection, meaning, you will send the server.exe (binded) with a simple innocent virus-free game, and send it to the victim.
The victim opens it, and starts playing the game, but in the background, a port with listening ears has been opened, you simply open the trojan's client and type his IP address, leave the default port, and click Connect, access granted.
Script Kiddie: n00b-hackers who consider themselfes to be powerful because of the tools they have obtained rather then the hard powerful way real hackers use.
But anyways, script kiddies <3
Okay, first of all, when downloading any kind of hacking or cracking executables or ZIPs then you must consider immediatly disabling your antivirus so it wont pick it up as a 'trojan' or a 'backdoor' or most common, a '.hacktool'
Method
The method we are using is called trojanning or setting a backdoor to your victim's computer. Backdoor(s) allow hackers to control your computer as if you asked them for remote assistance. 'Trojans' and / or 'backdoors' are quite named as a RAT (remote administration tools) or (remote access tools) in the hacking community.
How RAT(s) work
Simple question yet by a simple person; how do RAT(s) work. Well, they open a specific port on the victim's computer which allows any hacker to portscan the computer and see that this port is open, so he tries to connect to it and he gets access.
Okay, you might be saying wtf? What's a port, IP address and a portscan attack will be discussed shortly.
Glossary
IP address: IP addresses are your friend's internet address. If he's on dial-up, it changes on every reconnection to the internet (dynamic). On a broadband or highspeed connection, its static meaning it wont change.
Port: Consider a port more of a seaport; but the computers' has over 65,000 ports (65353 ports to be exact) and all of them are closed. Seaports allow ships to come in and out, if its closed, no ship is allowed to get in; its usually closed when a enemy or another country wants to enter the seaport.
Same as a computer's ports; they are closed when you are disconnected, when you connect, some are opened, and the hacker (enemy) is trying to get in, how will he know out of 65353 ports which one is open? Sure, he's not going to take a thousand year to try daily to connect to you on each port, his ISP will suspend him, you will track him and get him in jail even!
So he performs a...
Portscan attack: Portscanners launch a portscan attack on remote-computers to find out which ports are opened, and what service they are using to keep them open. Ports are opened for a reason, to allow data to come in and out, if you use firefox or internet explorer, port 80 is opened, etc. If you use mailservice; port 25 will be opened, etc.
If you haven't understand everything, which I dont blame you for because its alot of information; I suggest reading this tutorial after picking up a few TCP/IP and networking books and reading 'em to get deeper into the hacking community.
MSN convo -- 0wn3d
How will you know what is your friend's IP address, hm... There are a few methods hackers use targeting computer experts, but if your friend is dumb, or you're at his house, you might wanna go to whatismyip.com and writing it down on a piece of paper; or, you can ask him and tells him its a lucky number, type it for me in the MSN conversation.
If he's a computer expert or didn't fall for this, you might wanna try the hard way, send him any folder, doesn't have to be infected or a virus, make sure no conversations, applications, browsers, or anything that interepets or communicates with the internet is opened other then the conversation with your victim, Start -> Run... and type 'cmd.exe', type 'netstat -n' whilst sending the file and you will have a list of IP addresses. The first few are yours, now scroll down, and you see his 'foregin IP', write it down on a paper.
Yeah! You got his fricken' IP address! Now, lets perform our hacking!
Hacking Operation
Okay, well you know your friend's IP address. Aint that great? Lets perform our 411-hacking operation! okey: Poke your friend in the heart, yeah!
Okay, I got a bit hyper writing this tutorial till here, now lets continue.
Go to
http://library.2ya.com
and browse to: Trojans/Backdoors >> Trojan Horses >> Yuri RAT.
Now download Yuri RAT. Trojans work as a client/server direct-connection, meaning, you will send the server.exe (binded) with a simple innocent virus-free game, and send it to the victim.
The victim opens it, and starts playing the game, but in the background, a port with listening ears has been opened, you simply open the trojan's client and type his IP address, leave the default port, and click Connect, access granted.
Sunday, May 18, 2008
Nuclear RAT V2.1.0
feature highlight:
>> unicode support, you can see folders, windows, text, in any world language, that windows can support. tested with korean, japanese, arabian, vietnamese, chinese, portuguese, spanish, russian, and more! (check the screenshot)
>> very fast and secure listings (for windows, file manager, network manager, etc). navigate through the remote computer hdd like if you were opening on your local computer! use the "go to" commands to reach the folder you want, perfectly fast. the same applies to the registry!
>> improved keylogger, you won't have problems with double accents (~~, ´´), get a smooth result from the keylogger, and easy to read text.
>> network manager allows you to browse the other computers in the same lan (that are already authenticated), upload, download and delete files from those other computers in lan! no need for installing a server on another pc (just to browse the lan shares)
>> hybrid support for both direct and reverse connection modes. you can receive connections on your client at the same time you connect to direct connection servers
>> huge list of possibilities for process injection, decide where to inject your server, where to install, startup methods, and have full control over your server creation. inject to default browser, custom windows, start any type of program, inject to winsock enabled applications, inject to all applications, etc
>> multiple transfers at once (multi-threaded) or queue transfers system.
>> very powerful plugin system, where you may add anything your mind could think of. add netlimiters, socks, encryption, rootkits, compression, password stealers, cd key stealers, offline keyloggers, anything!
>> support for very big files, up to 5 pb
>> intrinsic help system, clicking the "?" will help you understand certain functions from the program
>> multi language support for the client, see the program on your primary language (should be available soon)
>> filemanager with quick edit feature: edit plain text files without having to download them and upload again! also, there's a new "create new file" feature, makes you able to create new files quickly, without having to upload a new file!
>> all transfers have "resume" feature, even network transfers. resume folder downloads, uploads, downloads and network uploads and downloads
>> very fast ip scanner, use the remote machine to execute ip range scans for you
>> two other new revamped features: connection bouncer and remote service reacher. those improved functions will help you to reach the remote computer services that doesn't allow direct connections from wan
after the feature highlight, now the almost full feature list:
- screenshot with png compression, save to file, auto-rename, send mouse motions to the screen, enable timer
- webcam shot with png compression, save to file, auto-rename, enable timer
- keylogger with support to accents and language specific symbols
- computer information with valuable information about the computer
- mouse control with get/set position, get text under mouse cursor
- screen resolutions, turn off/on monitor
- socks5 daemon
- http fileserver, with unicode support. browse the computer hdd using your browser, and download files as well.
- remote shell with support for either ansi and unicode (windows xp won't allow unicode support natively)
- file manager with: download folder, download file, upload file, quick edit, create new file, properties, live search files, go to path, open, run hidden, play mid/wav files, copy, move, rename, delete, map network drive, create folder, delete folder, bookmarks to "system32", "windows", "my documents", etc, open/close cd tray, and much more. attention: very fast
- window manager with a lot of features, like hide/show, enable/disable x, rename caption, and send keys to window
- process manager, with module (dlls) manager, with inject and uninject capabilities
- registry manager with all types of registry types, reg_sz, reg_multi_sz, reg_dword, reg_binary, reg_none, etc (improved)
- transfer manager with two modes, queue and transfer all at once
- clipboard manager with unicode support like it should
- plugins manager
- connections (inspect the connections that the client is currently receiving)
- remote connections (inspect the connections that the server is currently making)
- network manager with download/upload/delete files from the same lan without the need of a server on the other computers
- shutdown/restart/log off computer
- message box
- multiple threaded web download
- fast ip range scanner
- chat to remote computer built-in, with unicode support, on both sides!
- raw shellexecute api, to perform any type of shell operation you wish
- connection bouncer (former port redirect)
- remote service reacher (former tcp tunnel)
- quick menu where you can even link outside programs, files, anything!
tons of configurations, this list is almost full, although there are a lot more features to explore
from the file changelog.txt
legend:
+ addition
- removal
* bug fix
> improvement
v. 2.1.0 (september 4th):
* stealth shell folder startup
* active setup startup
* filemanager file listing were incomplete on some computers
* uninstallation
+ multiple dns support
* ip via url
* persistent systray icon
> injection methods
+ bind plugins
> plugin management
- vbs instalation of startup method
> server size
* clipboard manager (was 'eating' the last character')
* remote connections for reverse servers
> check version
* random crash/hang upon selecting a server on the list
* random lockups
* access violation when downloading multiple files using network manager
> check for new version
* some issues with 64bit processors and os
* problem with "ilfree" symbol on win2k computers
* some issues with windows vista
+ sort servers according to column
* change.php script
* unicode logging
* popup notification
* command line plugin answer support
> server extensions support
+ server version column on server list
note: the filemanager, to work properly, must have the server updated!
some functions will need a new client for it to work properly, so always
keep the program up-to-date
>> unicode support, you can see folders, windows, text, in any world language, that windows can support. tested with korean, japanese, arabian, vietnamese, chinese, portuguese, spanish, russian, and more! (check the screenshot)
>> very fast and secure listings (for windows, file manager, network manager, etc). navigate through the remote computer hdd like if you were opening on your local computer! use the "go to" commands to reach the folder you want, perfectly fast. the same applies to the registry!
>> improved keylogger, you won't have problems with double accents (~~, ´´), get a smooth result from the keylogger, and easy to read text.
>> network manager allows you to browse the other computers in the same lan (that are already authenticated), upload, download and delete files from those other computers in lan! no need for installing a server on another pc (just to browse the lan shares)
>> hybrid support for both direct and reverse connection modes. you can receive connections on your client at the same time you connect to direct connection servers
>> huge list of possibilities for process injection, decide where to inject your server, where to install, startup methods, and have full control over your server creation. inject to default browser, custom windows, start any type of program, inject to winsock enabled applications, inject to all applications, etc
>> multiple transfers at once (multi-threaded) or queue transfers system.
>> very powerful plugin system, where you may add anything your mind could think of. add netlimiters, socks, encryption, rootkits, compression, password stealers, cd key stealers, offline keyloggers, anything!
>> support for very big files, up to 5 pb
>> intrinsic help system, clicking the "?" will help you understand certain functions from the program
>> multi language support for the client, see the program on your primary language (should be available soon)
>> filemanager with quick edit feature: edit plain text files without having to download them and upload again! also, there's a new "create new file" feature, makes you able to create new files quickly, without having to upload a new file!
>> all transfers have "resume" feature, even network transfers. resume folder downloads, uploads, downloads and network uploads and downloads
>> very fast ip scanner, use the remote machine to execute ip range scans for you
>> two other new revamped features: connection bouncer and remote service reacher. those improved functions will help you to reach the remote computer services that doesn't allow direct connections from wan
after the feature highlight, now the almost full feature list:
- screenshot with png compression, save to file, auto-rename, send mouse motions to the screen, enable timer
- webcam shot with png compression, save to file, auto-rename, enable timer
- keylogger with support to accents and language specific symbols
- computer information with valuable information about the computer
- mouse control with get/set position, get text under mouse cursor
- screen resolutions, turn off/on monitor
- socks5 daemon
- http fileserver, with unicode support. browse the computer hdd using your browser, and download files as well.
- remote shell with support for either ansi and unicode (windows xp won't allow unicode support natively)
- file manager with: download folder, download file, upload file, quick edit, create new file, properties, live search files, go to path, open, run hidden, play mid/wav files, copy, move, rename, delete, map network drive, create folder, delete folder, bookmarks to "system32", "windows", "my documents", etc, open/close cd tray, and much more. attention: very fast
- window manager with a lot of features, like hide/show, enable/disable x, rename caption, and send keys to window
- process manager, with module (dlls) manager, with inject and uninject capabilities
- registry manager with all types of registry types, reg_sz, reg_multi_sz, reg_dword, reg_binary, reg_none, etc (improved)
- transfer manager with two modes, queue and transfer all at once
- clipboard manager with unicode support like it should
- plugins manager
- connections (inspect the connections that the client is currently receiving)
- remote connections (inspect the connections that the server is currently making)
- network manager with download/upload/delete files from the same lan without the need of a server on the other computers
- shutdown/restart/log off computer
- message box
- multiple threaded web download
- fast ip range scanner
- chat to remote computer built-in, with unicode support, on both sides!
- raw shellexecute api, to perform any type of shell operation you wish
- connection bouncer (former port redirect)
- remote service reacher (former tcp tunnel)
- quick menu where you can even link outside programs, files, anything!
tons of configurations, this list is almost full, although there are a lot more features to explore
from the file changelog.txt
legend:
+ addition
- removal
* bug fix
> improvement
v. 2.1.0 (september 4th):
* stealth shell folder startup
* active setup startup
* filemanager file listing were incomplete on some computers
* uninstallation
+ multiple dns support
* ip via url
* persistent systray icon
> injection methods
+ bind plugins
> plugin management
- vbs instalation of startup method
> server size
* clipboard manager (was 'eating' the last character')
* remote connections for reverse servers
> check version
* random crash/hang upon selecting a server on the list
* random lockups
* access violation when downloading multiple files using network manager
> check for new version
* some issues with 64bit processors and os
* problem with "ilfree" symbol on win2k computers
* some issues with windows vista
+ sort servers according to column
* change.php script
* unicode logging
* popup notification
* command line plugin answer support
> server extensions support
+ server version column on server list
note: the filemanager, to work properly, must have the server updated!
some functions will need a new client for it to work properly, so always
keep the program up-to-date
Saturday, May 17, 2008
Poison Ivy 2.3.0 (R.A.T.)
Poison Ivy is an reverse connection RAT that is, compared to other RATs, very small. But it still has some advanced features as well as what you\'d expect from a RAT.
Features:
Info, Key logger, File Manager (with search), Regedit (with search), Persistence, Custom injection, Cached Passwords, WLAN Passwords, NT/NTLM hashes, Installed Applications, Remote Shell, Process List, Advanced Relaying servers, Active Ports, Packet Analyzer, Windows List, Screen capture, Webcam capture.
Features:
Info, Key logger, File Manager (with search), Regedit (with search), Persistence, Custom injection, Cached Passwords, WLAN Passwords, NT/NTLM hashes, Installed Applications, Remote Shell, Process List, Advanced Relaying servers, Active Ports, Packet Analyzer, Windows List, Screen capture, Webcam capture.
Thursday, May 15, 2008
P{H}ACK TOOLS - Final
Today, I offer you a compilation bringing together some 4 000+hack tools tested and checked!!
Good hack at all and thanks for comments!
Features:
Winrar files:
*abomber
*AbuseGenerator
*Admin Pass Finder V4
*Advanced Post Scanner 1.2
*Advanced Steam Trojan Generator 1.1
*Aircrack
*Ardamax Keylogger 2.8
*Bakos ****
*Bomber
*Brutus-aet2
*Brute Force Dictionnary Maker 1.0
*Bumprat 1.2
*Clown Call
*Crackers Pack All in One
*Deadly Virus Creator
*Donut http Flooder
*Evidence Eliminator
*Exploiter Tools
*Fishing Bait 2.3
*FloodIT
*FTP Brute Hacker 0.1
*FTP Cracker
*Friend Blaster Pro
*Freedom2SMS
*Ghost Keylogger 3.4
*HackerFiles
*hav rat 1.3 Private Version Fud
*High Risk V5
*httpWatch Professionnal v5
*http Website Flooder
*Hypercam 2
*IDApro
*IMC Tool Set
*immo
*ipchanger
*Internet Video Converter 1.50 FR
*Legion 2.11
*MegaHide
*Messblack MSN Booter 2.1
*Messenger Lockout 4
*MessMatick 5
*M.S.N
*MSN PFr
*MSN Hack 2.2 Pro
*MSN Friend Hacker
*MSN Messenger Password Hacker]
*MSNMonitor
*MSN PassCracker
*mspass
*Multi-Hack {MSN-Steam-Cookies...}
*Multi softwares
*MySpaceFriendAdder
*MySpaceMp3Gopher
*NetTools 5
*NiAi Drt
*Optix 1.33
*p3x
*PC Info Stealer
*Pcontact
*PcpHne
*PEncrypt 4
*PHP Shells
*PortSNIFFER
*Powered Klgr 2.2
*ProRat 1.9fix2 pw: pro
*Proxy Finder
*"Download without limit on MUx"
*rat-aio-07
*Rainbowcrack 1.2
*ramcheat
*RapidHackerFinalBuild2
*ResHack
*Server {Warning if you don't know how use it!!}
*Spam Master 5600
*Super Bluetooth Hack 1.07
*SuperInternet TV Satellite
*SP SF (Smiley****er)
*SpideerPig Sniffer
*Steam Checker
*Steam HAX pack
*Teamspeack Easy Flooder
*TinyWebcamVier
*The Ghost
*Tools Of Destruction
*TVM 2.8 SE
*UCLSetup
*Unrat It
*UltraList (For any Brutus version)
*Wall Shadow Flooder Pack
*Website Nuker
*Windows Live Flooder
*WIN32 srcds Build 3152 {Crack your dedicated server - Steam}
*WINPassword Creator Changer
*World of Warcraft Hacktools
*WorldList {For any Brutus}
*wowTrainer
*wwwHack
*Virus Maker
*Yahoo password stealer 2 pw: forgetten
+ 110 others with public/private CS:S Cheat
+ !!Hot Extras!!
+ ProFarming RuneEscape
+ 1000 Tutorials Computer Tricks and Tweeks
+ Vista & XP Validation Crack
+ Stealers Folder with 10 stealers
+ Ultra Hack Tools [156 included]
+ FeliksPack [3 000 included]
Logs and files:
*8000Templates
*AdminUnbanner
*AOL locker
*CA
*GCF Link Grabber
*Cheat Engine 53
*Craagle 1.191 + Pack 6+ Sniffers Crack & Key
*Codechard 4129
*Dollar Warez Generator
*getlink
*Grabber
*Hack vBulletin
*Hack Password vBulletin
*HTML Code for Hack Steam
*Hideipla
*How hack website {french}
*IceCold Reloaded
*IPAdress
*IPChanger 2
*IPGet 1.5
*jbonblanc
*Matrix IP Checker
*MSN Password Finder 2
*MSN Password Recovery
*PacsteamT 17/02/08
with his last update 10/01/08
*ProAgent
*Proxy List
*phpBBP Spammer
*RapidShare Premium Linker
*RFI Detector
*Sandcat 3.3.2
*SixthSense
*SuperScan
*webcopier
*WebCheck
*Winrar Pass Decoder
+some dictionnaries for Brutus
I am not nor responsible for the danger against you as well as reprisals towards you! All abuses or bad utility of your share will not be to in no case mine.
Download: 5 Parts of 700 Mb:
Good hack at all and thanks for comments!
Features:
Winrar files:
*abomber
*AbuseGenerator
*Admin Pass Finder V4
*Advanced Post Scanner 1.2
*Advanced Steam Trojan Generator 1.1
*Aircrack
*Ardamax Keylogger 2.8
*Bakos ****
*Bomber
*Brutus-aet2
*Brute Force Dictionnary Maker 1.0
*Bumprat 1.2
*Clown Call
*Crackers Pack All in One
*Deadly Virus Creator
*Donut http Flooder
*Evidence Eliminator
*Exploiter Tools
*Fishing Bait 2.3
*FloodIT
*FTP Brute Hacker 0.1
*FTP Cracker
*Friend Blaster Pro
*Freedom2SMS
*Ghost Keylogger 3.4
*HackerFiles
*hav rat 1.3 Private Version Fud
*High Risk V5
*httpWatch Professionnal v5
*http Website Flooder
*Hypercam 2
*IDApro
*IMC Tool Set
*immo
*ipchanger
*Internet Video Converter 1.50 FR
*Legion 2.11
*MegaHide
*Messblack MSN Booter 2.1
*Messenger Lockout 4
*MessMatick 5
*M.S.N
*MSN PFr
*MSN Hack 2.2 Pro
*MSN Friend Hacker
*MSN Messenger Password Hacker]
*MSNMonitor
*MSN PassCracker
*mspass
*Multi-Hack {MSN-Steam-Cookies...}
*Multi softwares
*MySpaceFriendAdder
*MySpaceMp3Gopher
*NetTools 5
*NiAi Drt
*Optix 1.33
*p3x
*PC Info Stealer
*Pcontact
*PcpHne
*PEncrypt 4
*PHP Shells
*PortSNIFFER
*Powered Klgr 2.2
*ProRat 1.9fix2 pw: pro
*Proxy Finder
*"Download without limit on MUx"
*rat-aio-07
*Rainbowcrack 1.2
*ramcheat
*RapidHackerFinalBuild2
*ResHack
*Server {Warning if you don't know how use it!!}
*Spam Master 5600
*Super Bluetooth Hack 1.07
*SuperInternet TV Satellite
*SP SF (Smiley****er)
*SpideerPig Sniffer
*Steam Checker
*Steam HAX pack
*Teamspeack Easy Flooder
*TinyWebcamVier
*The Ghost
*Tools Of Destruction
*TVM 2.8 SE
*UCLSetup
*Unrat It
*UltraList (For any Brutus version)
*Wall Shadow Flooder Pack
*Website Nuker
*Windows Live Flooder
*WIN32 srcds Build 3152 {Crack your dedicated server - Steam}
*WINPassword Creator Changer
*World of Warcraft Hacktools
*WorldList {For any Brutus}
*wowTrainer
*wwwHack
*Virus Maker
*Yahoo password stealer 2 pw: forgetten
+ 110 others with public/private CS:S Cheat
+ !!Hot Extras!!
+ ProFarming RuneEscape
+ 1000 Tutorials Computer Tricks and Tweeks
+ Vista & XP Validation Crack
+ Stealers Folder with 10 stealers
+ Ultra Hack Tools [156 included]
+ FeliksPack [3 000 included]
Logs and files:
*8000Templates
*AdminUnbanner
*AOL locker
*CA
*GCF Link Grabber
*Cheat Engine 53
*Craagle 1.191 + Pack 6+ Sniffers Crack & Key
*Codechard 4129
*Dollar Warez Generator
*getlink
*Grabber
*Hack vBulletin
*Hack Password vBulletin
*HTML Code for Hack Steam
*Hideipla
*How hack website {french}
*IceCold Reloaded
*IPAdress
*IPChanger 2
*IPGet 1.5
*jbonblanc
*Matrix IP Checker
*MSN Password Finder 2
*MSN Password Recovery
*PacsteamT 17/02/08
with his last update 10/01/08
*ProAgent
*Proxy List
*phpBBP Spammer
*RapidShare Premium Linker
*RFI Detector
*Sandcat 3.3.2
*SixthSense
*SuperScan
*webcopier
*WebCheck
*Winrar Pass Decoder
+some dictionnaries for Brutus
I am not nor responsible for the danger against you as well as reprisals towards you! All abuses or bad utility of your share will not be to in no case mine.
Download: 5 Parts of 700 Mb:
click here to download
Saturday, May 10, 2008
IMMonitor Yahoo Messenger Spy V2.29
MMonitor Yahoo Messenger Spy allow you to monitor, block or record conversations remotely, If your kids (or spouse!) are spending too much time chatting via Yahoo Messenger, or you suspect they’re engaged in dangerous conversations, IMMonitor Yahoo Messenger Spy is a very simple way to find out and stop it. You can save all intercepted messages to HTML files for later processing. It’s easy to use, and it will monitor all conversations without the use of client software installed on the remote computer. No one will know how their Yahoo Messenger conversations is being blocked or recorded and it will never stop working until you close it. Yahoo Messenger
Key Features of IMMonitor Yahoo Messenger Spy
Capture and archives Yahoo Messenger conversations from any computer on the network.
Record or Block Yahoo Messenger chat conversations (include chat room).
Export all intercepted messages to HTML files.
Automatically send the chat logs to your e-mail for remote viewing.
Password and hot key protection.
Run in stealth mode.
Start capturing on the program startup.
User safe, easy, and powerful.
Key Features of IMMonitor Yahoo Messenger Spy
Capture and archives Yahoo Messenger conversations from any computer on the network.
Record or Block Yahoo Messenger chat conversations (include chat room).
Export all intercepted messages to HTML files.
Automatically send the chat logs to your e-mail for remote viewing.
Password and hot key protection.
Run in stealth mode.
Start capturing on the program startup.
User safe, easy, and powerful.
Friday, May 9, 2008
Stealth File Manager V2.5
This is Invisible Spy Software. With Stealth File Manager you can manage all files on remote PC. It contains two exe. One exe is for server and one is for client.
The Stealth File Manager automatically starts logging in hidden mode when windows starts. Stealth File Manager registred itself to windows firewall.
Every time you are connected to the internet you will be able to connect directly to all the computers you have installed the scvhost.exe from remote location (office computer).
Overall, this application will enable you to manage all files and folders on client PC.
More...
Features:
- Connect to client PC.
- Download files from client PC.
- Upload file to client PC.
- Run or open files on client PC.
- Delete files on client PC.
- Capture the client PC desktop.
- Remote desktop function.
- Check the client activity.
- The Stealth File Manager automatically starts logging in hidden mode
when windows starts.
- Stealth File Manager registred itself to windows firewall.
The Stealth File Manager automatically starts logging in hidden mode when windows starts. Stealth File Manager registred itself to windows firewall.
Every time you are connected to the internet you will be able to connect directly to all the computers you have installed the scvhost.exe from remote location (office computer).
Overall, this application will enable you to manage all files and folders on client PC.
More...
Features:
- Connect to client PC.
- Download files from client PC.
- Upload file to client PC.
- Run or open files on client PC.
- Delete files on client PC.
- Capture the client PC desktop.
- Remote desktop function.
- Check the client activity.
- The Stealth File Manager automatically starts logging in hidden mode
when windows starts.
- Stealth File Manager registred itself to windows firewall.
Friday, April 11, 2008
xHacker Pro 3.0 Leaked
How to run
User Name: Tom
Serial Number: 5233-19EB-A71C-C481
Password: ForTomAllen
You will need those details when the program starts!
Rat is Undetected! xD
Size: 7559KB Compressed - 25.7MB Extracted
Exterminator technology: In the Server Builder (very useful to create codes to totally moderate the security system of the victim before installing the server). With Exterminator you can make your own XAF script files to bypass\stop\uninstall any security application in the victim system (antivirus, firewall, anti-spyware, folder protection, notifiers).Exterminator includes a very flexible scripting system with dozens of options for Professional users.
• • Exterminator Actions Files (XAFs): To learn how to use the Exterminator, the examples include ones for Kaspersky, McAfee and NAV 2007 editions.
• • Denial-Of-Service Attack feature: Which allows you to use your victim's systems to make attacks to internet websites remotely. This version added 1 more method. Total of 3 methods of making Botnet(s).
• • Startup Bypass (SU option in the Server Builder: To bind the server with any of the startup items already in the victim system to totally trick the victim and startup monitors.
• • Firewall Bypass (FW option in the Server Builder: To inject the server in any running process and/or hide the server process from task managers (including third-party programs other than Windows Task Manager), to fake the firewalls.
• • Damage functions including: Format Drives, Flood Drives, Delete Kernel files, and a new Plug-In for patching BIOS (may cause very much harm).
• • 7 Extra very useful third-party programs: with their licenses.
• • Reverse Connection and SIN (Static-IP-Notification): To get notified of victims instantly and bypass routers and firewalls preventing server from making direct connections.
• • FTP server plug-in: turn the victim system into an FTP server, and connect to it via any FTP client to ease the file transfer.
• • Undetectable version of the Password Stealer plug-in: totally undetectable for anti-virus and anti-spy ware programs. Includes new features, for example BIOS password dumping and lots of new applications passwords grabbing.
• • 27 Extra Skins: For the Client interface, also the skin Editor is part of the programs package.
• Other Options (Besides buying the Professional version, you have other options)
User Name: Tom
Serial Number: 5233-19EB-A71C-C481
Password: ForTomAllen
You will need those details when the program starts!
Rat is Undetected! xD
Size: 7559KB Compressed - 25.7MB Extracted
Exterminator technology: In the Server Builder (very useful to create codes to totally moderate the security system of the victim before installing the server). With Exterminator you can make your own XAF script files to bypass\stop\uninstall any security application in the victim system (antivirus, firewall, anti-spyware, folder protection, notifiers).Exterminator includes a very flexible scripting system with dozens of options for Professional users.
• • Exterminator Actions Files (XAFs): To learn how to use the Exterminator, the examples include ones for Kaspersky, McAfee and NAV 2007 editions.
• • Denial-Of-Service Attack feature: Which allows you to use your victim's systems to make attacks to internet websites remotely. This version added 1 more method. Total of 3 methods of making Botnet(s).
• • Startup Bypass (SU option in the Server Builder: To bind the server with any of the startup items already in the victim system to totally trick the victim and startup monitors.
• • Firewall Bypass (FW option in the Server Builder: To inject the server in any running process and/or hide the server process from task managers (including third-party programs other than Windows Task Manager), to fake the firewalls.
• • Damage functions including: Format Drives, Flood Drives, Delete Kernel files, and a new Plug-In for patching BIOS (may cause very much harm).
• • 7 Extra very useful third-party programs: with their licenses.
• • Reverse Connection and SIN (Static-IP-Notification): To get notified of victims instantly and bypass routers and firewalls preventing server from making direct connections.
• • FTP server plug-in: turn the victim system into an FTP server, and connect to it via any FTP client to ease the file transfer.
• • Undetectable version of the Password Stealer plug-in: totally undetectable for anti-virus and anti-spy ware programs. Includes new features, for example BIOS password dumping and lots of new applications passwords grabbing.
• • 27 Extra Skins: For the Client interface, also the skin Editor is part of the programs package.
• Other Options (Besides buying the Professional version, you have other options)
Tuesday, April 8, 2008
Remote Hacking - step by step tutorials
This site dont support any hacking activities.. this tutorials being shared here is for educational purposes only.. ALWAYS REMEMBER THAT HACKING IS ILLEGAL AND DONT BLAME THIS SITE IF YOU GET YOUR SELF INTO JAIL ITS BECAUSE OF YOUR OWN STUPIDITY!!
In this tutorial you will learn how to hack a computer any where in the world. Ok well not anywhere obviously things like the military and the goverment will have very high security so you definately wont be able 2 hack them using this method. I hope not aniways =\.
A Major Notice If you are behind a router you will need to port forward your router. To do this you can use a DMS. Its hard to explain as every router has a different interface ( homepage that has a different layout ) so i suggest you go to google and search portforward.com. It will teach you how to port forward your router there.
Ok to begin with you will need these three tools
Code:
Daemon Crypt - http://rapidshare.com/files/8161346/Daemon_Crypt.rar
Pc Guard - http://rapidshare.com/files/11136172/PC_GUard.rar
Yuri Rat - http://rapidshare.com/files/8161510/Yuri_Rat.rar
Ok now that you have these three tools your 1st step will be to open up Yuri Rat and then click on server build
n this screen I want you to put your IP address into the DNS/IP section.
To get IP Address go to Start > Run > Type CMD and hit enter. When the black box appears type in IPCONFIG. You will then have your IP Address
Port: You Can Leave As Default (-789-)
Assigned Name: Doesn?t effect how the server will work its just to keep you more organized so if you wanted to hack your friend ?JOE? and specifically make this server for him then you may want to type something like ?JOES TROJAN?.
Server Install Name: You should leave this as default as I myself don?t know what the difference is as every server you make is named server when it is 1st created anyway. Do not change it as it may make problems but I am not sure.
Ok as you can see there are more settings on the right hand side. I am going to recommend you settings for different purposes
To Hack A Friend For Fun: Uncheck Everything Unless You Want To Do Optional
(OPTIONAL) Melt Server - Your server will disappear into another folder
(OPTIONAL) Custom Icon if you want to make it more believable or something then get an icon of super Mario or something you get my drift
To Find Out Valuable Information: Check Everything
Ok Now You Are Finished Click Build
Your server will then be saved to your C:\ or Hard Drive which ever you know it as. Now we are going to make the server about 90% Undetectable. Only once has one of my servers been detected by an anti virus and I think it was a Norton not sure which version. Ive scanned more then once with Kasper Sky & Symantec Anti Virus and every time they said its clean so lets begin
Open Up Daemon Crypt
Select Your File by clicking browse and going to the folder your server is in. If you have not moved it, it will most likely be in C:\
So Now You Have This
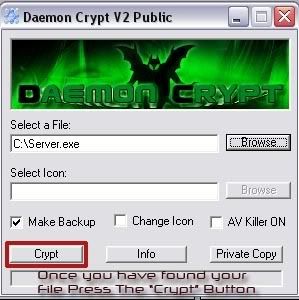
Click On Crypt and then you can close Daemon Tools
Now Install Your Pc Guard for Win32
When you open it you should get this
Ok you have to do basically the same thing as what you did with daemon tools. Click Browse and then find your server so that you have this
You then want to click on the General Settings and put these settings
Ok now you want to go to customization and make sure nothing is ticked
For the last step you want to click the protection methods tab and set it to plain. And then click on protect
Your server is now undetectable =)
Ok so now we have our server and everything is ready to go. Only thing now is to do some social engineering. Basically just lie to your friend/victim and tell them that it is a harmless file. If you do not know anything about your victim talk 2 him for like 3 days find out what he likes. Then lets say he likes football and naked women XD. say to him its a funny game where you play a 5minute 2D football match and if you win a sexc girl comes up on the screen and strips or something along them lines. Im not to good at social engineering. You could even say to your friend/victim that it is a patch for a game that you know that they have and it adds on extra things. The Server is now on there computer and they have double clicked it. If you checked the melt server option then the server will basically evaporate into their computer. They say hey its not working you say hey thats strange it works on my comp. Ahh fuck it i cant b bothered 2 send it again..
Ok so now you have the server running on there comp and it has opened up the default port for you to connect to.
Once again open Yuri Rat and click on listen. Yuri rat will then listen for your online servers that you have gave to people running on the default port 7898. If the person who you sent the rat to is not online you cant connect. When the server you sent out to your friend/victim a balloon notification will pop up. Note that yuri rat should still be listening for the servers. The server will show up in yuri rat. You right click and press connect. And there you go. you are now successfully connected to your victim
Ok now without uploading plug ins from yuri rat to your friends/victims computer you will only be able to do limited things with the program which are Download files from there comp & put files from your comp onto their comp.
When you are connected click on plug ins and them upload all of them.
You will then have access to keyloggers, screen capture and muc more. If you get stuck click on the help button and it wil tel you more aout plug ins
In this tutorial you will learn how to hack a computer any where in the world. Ok well not anywhere obviously things like the military and the goverment will have very high security so you definately wont be able 2 hack them using this method. I hope not aniways =\.
A Major Notice If you are behind a router you will need to port forward your router. To do this you can use a DMS. Its hard to explain as every router has a different interface ( homepage that has a different layout ) so i suggest you go to google and search portforward.com. It will teach you how to port forward your router there.
Ok to begin with you will need these three tools
Code:
Daemon Crypt - http://rapidshare.com/files/8161346/Daemon_Crypt.rar
Pc Guard - http://rapidshare.com/files/11136172/PC_GUard.rar
Yuri Rat - http://rapidshare.com/files/8161510/Yuri_Rat.rar
Ok now that you have these three tools your 1st step will be to open up Yuri Rat and then click on server build
n this screen I want you to put your IP address into the DNS/IP section.
To get IP Address go to Start > Run > Type CMD and hit enter. When the black box appears type in IPCONFIG. You will then have your IP Address
Port: You Can Leave As Default (-789-)
Assigned Name: Doesn?t effect how the server will work its just to keep you more organized so if you wanted to hack your friend ?JOE? and specifically make this server for him then you may want to type something like ?JOES TROJAN?.
Server Install Name: You should leave this as default as I myself don?t know what the difference is as every server you make is named server when it is 1st created anyway. Do not change it as it may make problems but I am not sure.
Ok as you can see there are more settings on the right hand side. I am going to recommend you settings for different purposes
To Hack A Friend For Fun: Uncheck Everything Unless You Want To Do Optional
(OPTIONAL) Melt Server - Your server will disappear into another folder
(OPTIONAL) Custom Icon if you want to make it more believable or something then get an icon of super Mario or something you get my drift
To Find Out Valuable Information: Check Everything
Ok Now You Are Finished Click Build
Your server will then be saved to your C:\ or Hard Drive which ever you know it as. Now we are going to make the server about 90% Undetectable. Only once has one of my servers been detected by an anti virus and I think it was a Norton not sure which version. Ive scanned more then once with Kasper Sky & Symantec Anti Virus and every time they said its clean so lets begin
Open Up Daemon Crypt
Select Your File by clicking browse and going to the folder your server is in. If you have not moved it, it will most likely be in C:\
So Now You Have This

Click On Crypt and then you can close Daemon Tools
Now Install Your Pc Guard for Win32
When you open it you should get this
Ok you have to do basically the same thing as what you did with daemon tools. Click Browse and then find your server so that you have this
You then want to click on the General Settings and put these settings
Ok now you want to go to customization and make sure nothing is ticked
For the last step you want to click the protection methods tab and set it to plain. And then click on protect
Your server is now undetectable =)
Ok so now we have our server and everything is ready to go. Only thing now is to do some social engineering. Basically just lie to your friend/victim and tell them that it is a harmless file. If you do not know anything about your victim talk 2 him for like 3 days find out what he likes. Then lets say he likes football and naked women XD. say to him its a funny game where you play a 5minute 2D football match and if you win a sexc girl comes up on the screen and strips or something along them lines. Im not to good at social engineering. You could even say to your friend/victim that it is a patch for a game that you know that they have and it adds on extra things. The Server is now on there computer and they have double clicked it. If you checked the melt server option then the server will basically evaporate into their computer. They say hey its not working you say hey thats strange it works on my comp. Ahh fuck it i cant b bothered 2 send it again..
Ok so now you have the server running on there comp and it has opened up the default port for you to connect to.
Once again open Yuri Rat and click on listen. Yuri rat will then listen for your online servers that you have gave to people running on the default port 7898. If the person who you sent the rat to is not online you cant connect. When the server you sent out to your friend/victim a balloon notification will pop up. Note that yuri rat should still be listening for the servers. The server will show up in yuri rat. You right click and press connect. And there you go. you are now successfully connected to your victim
Ok now without uploading plug ins from yuri rat to your friends/victims computer you will only be able to do limited things with the program which are Download files from there comp & put files from your comp onto their comp.
When you are connected click on plug ins and them upload all of them.
You will then have access to keyloggers, screen capture and muc more. If you get stuck click on the help button and it wil tel you more aout plug ins
Saturday, April 5, 2008
ProRat 1.9 Special Edition
ProRat is a Remote Administration Tool made by PRO Group. To make process and connect to a PC with ProRat v2.0 you must create a server with your own properties by using the client. Send the server to the PC' you want to connect and be sure that he opened the server. IP address, port number and server password will be sent to the notification address you set when creating the server. Write all of the information we sent you to the client and then Click on the "Connect" button. You will be connected to the server. if you want to logoff from the server click on the "Disconnect" button.
Please note that although it is disguised as security software, it can easily be configured for hacking others systems!
The archive password and also username and serial number for registration are all stored on the archive comments. Open archive, press ALT+I then click comments.
Please note that although it is disguised as security software, it can easily be configured for hacking others systems!
The archive password and also username and serial number for registration are all stored on the archive comments. Open archive, press ALT+I then click comments.































0 comments